With the value of highway and street construction in the US expected to grow to $175 billion in 2028, and a draft US Department of Transportation (USDoT) V2X deployment plan targeting V2X being deployed in 40% of the nation’s intersections by 2029, developing a strong foundation for digitization of roadways infrastructure is a more urgent priority than ever.
With increased digitization, reducing cyber risks is essential, as recently highlighted by the World Economic Forum.
Ensuring the cybersecurity of ITS (intelligent transportation systems) equipment is crucial, as cyber-attacks can have widespread consequences, affecting public safety and economic stability. This is a major concern for departments of transportation (DoTs), cities and roadway operators as they plan digitization programs to enhance safety, improve traffic flow, and address sustainability and climate change goals.
Cybersecurity encompasses many aspects, from the physical security of the roadside cabinet and the equipment inside, right through to the security of applications such as those controlling the phases of a traffic signal to prioritise emergency vehicles, for example. However, there are many challenges faced by operators as they tackle issues such as:
• Challenges in connecting large numbers of roadside systems across wide geographic areas, compounded by a shortage of skilled labour.
• The lack of a detailed and up to date inventory of connected systems.
• Challenges in managing and enforcing unified security policies across all sites.
• Limited physical space in cabinets and at the roadside to deploy additional hardware appliances to deliver cybersecurity capabilities.
Cisco works with roadways operators around the globe, many of whom have shared experiences concerning cyber incidents that have already happened. However, many of them have been aware of ongoing exposure of the network that supports their ITS systems, primarily due to bad practices and non-optimal network designs.
In our conversations with DoTs and roadways operators, 5 clear steps have emerged to reduce cyber risks for connected ITS equipment and address challenges that they face.
Step 1: Secure, reliable and resilient connectivity is a must
Connecting numerous ITS systems across both urban and rural areas requires enterprise-grade performance, security and industrial-strength reliability. High-performance ruggedized switches, cellular routers, and wireless access points are essential to meet the connectivity needs of large, diverse geographic areas.
Because there is a need to support various types of cellular connectivity across the network, it is important to be able to change WAN interfaces on routers without changing entire devices. This ensures that the routers can easily adapt to changes in available connectivity, and as they provide access to the network, they also need to be firewalls to protect critical roadside equipment.
Key capabilities include:
• Next-generation firewall (NGFW) with application awareness to filter traffic in real time and identify and control applications.
• Intrusion detection and prevention (IDS/IPS) to identify and block known threats and malicious activities.
• Advanced malware protection to identify and block both known and unknown threats from malicious files.
• URL filtering to block or allow users to access URLs based on allowed or block lists, reputation or web categories.
• DNS security to prevent infected assets from contacting malicious servers.
• Centralized management to unify security policies and simplify securing ITS equipment at roadsides and intersections at scale.

Step 2: Understand what ITS equipment is connected
Securing roadways infrastructure begins with having a detailed understanding of what is connected to the network, developing an inventory, and making sure that inventory is continually updated. Detailed information, including specifics such as device types, vendor details, serial numbers, software versions and more. Clearly, maintaining this information manually would be prohibitively labour-intensive and error prone, and so this step needs to be automated. The inventory provides the necessary information to build effective security policies into IT security tools, and drive compliance with security regulations.
Step 3: Take a zero-trust approach
Zero-trust is a crucial security principle in enterprise IT and extends to the world of connected ITS equipment. Essentially, zero-trust security ensures that no device is trusted to connect to a network by default, either from inside or outside an organisation. Verification is required for any device connecting to the network. Only specific devices should be granted access to the ITS network, and all other devices denied access by default. This approach blocks unauthorized access and must be built into networking equipment to protect infrastructure. But it doesn’t stop there. Additionally, zero-trust principles include continuously monitoring communications to verify trust and isolate compromised equipment.
Step 4: Enforce trust through network segmentation
Once a device has been granted access, roadways operators need to ensure that it communicates only with the resources it needs to in order to do its job, to reduce the risk if a system is compromised. Segmentation of the network controls how traffic flows between different parts. For example, network segmentation can separate surveillance cameras from traffic signal controllers. It can also prevent systems installed at intersection X communicating with those installed at intersection Y. This stops malicious traffic from moving between systems and helps to curb the impact of a breach.
Step 5: Enable easy-to-use secure remote access
ITS equipment is distributed across every city, region, and country. Enabling remote access for troubleshooting and upgrades is key to reducing operational costs and the knock-on effects of outages on congestion and road user safety. Whether traffic operations teams need to grant access to third parties or make it simple for their own technicians to manage connected equipment, they need a remote access solution that’s easy to implement and highly secure.
Roadways operators are starting to deploy Zero Trust Network Access (ZTNA) solutions to simplify the remote access workflow. To simplify processes, remote users should be able to log into a single portal where access policies are defined and enforced for the entire infrastructure, making it easy to control access and define credentials to address emergency situations. The portal should then communicate with routers and switches in the infrastructure to ensure that remote users are only granted access to selected equipment which they need to configure, not to the entire network.
Fitting everything into the roadside cabinet
In roadside cabinets, there is often little space to install equipment. This means that network devices need to be small enough to fit into limited space and easy to install at every location. The security capabilities outlined in steps 1 to 5 should be built into the network devices themselves, as there is limited space for hardware within the cabinets, and maintenance costs need to be minimized.

Reaching our destination
Even though most in the industry recognize that physical security for ITS systems is limited and creates risk, connecting ITS devices directly to the public internet is the primary cause of exposure when it comes to cybersecurity. Earlier solutions consisted of data networks with limited or no segmentation, often directly exposed to the public internet and with little or no consideration for cyber security.
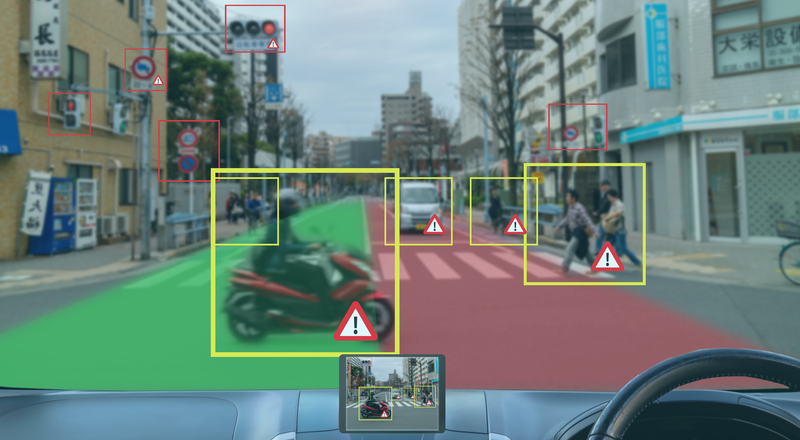
As density of ITS connectivity ramps up to address emerging use cases like connected and autonomous vehicles (C/AVs) and vulnerable road user (VRU) safety, the risk also increases almost exponentially, unless modern data networking and security best practices are adopted.
Achieving the goals of digital innovation in connected roadways and intersections requires a strong technical foundation.
As we have illustrated, connecting roadside equipment needs a solution that combines strong advanced cybersecurity capabilities with small form factor networking devices that can fit into a roadside cabinet and withstand the extreme environmental conditions at roadsides and intersections. To deliver the scale necessary to support huge numbers of intersections and systems, centralized management is key to simplify network deployment and unify security policies across the ITS infrastructure, so that there is no gap in defense.
Tried and tested, validated solutions for connected roadways and intersections are available today. Designed around small form factor ruggedized routers and switches with built in cybersecurity capabilities, these reference architectures are optimized to enhance ITS cyber-resilience.
Modern solutions reduce cyber risks and provide a scalable foundation to pave the way for new innovations like connected and autonomous vehicles, enhancing safety, improving traffic flow and delivering a more sustainable future.
Start your journey to secure ITS
For more than 20 years, Cisco has been helping organizations including DoTs and roadway operators around the globe digitize their operations. As we have explored in this article, key steps to achieving successful outcomes come down to adhering to a core set of key principles:
• Securely connect your ITS equipment using high performance, resilient connectivity which includes firewall protection.
• Understand what is connected to the network with a detailed inventory and ensure that it is continually updated.
• Enforce zero-trust so that no unverified device can gain access to your network.
• Segment your network to control which systems can communicate with each other.
• Provide secure remote access to ensure that only trusted individuals can access equipment for troubleshooting and upgrades.
• Network devices, which include the above security capabilities need to be ruggedized to withstand the environmental conditions at the roadside and intersection and must be able to fit into constrained spaces.
• Centralized management capabilities are required to provide control of security policies at scale across the network.
Learn more about how Cisco supports the successful digital transformation of roads, highways, and intersections on this web page.
Click here to watch our on-demand webinar and hear from our experts: Shielding the Future: Defending ITS and Roadways from Cyber Threats.  ABOUT THE AUTHORS
ABOUT THE AUTHORS
Pete Kavanagh is Principal Architect, Roadways Solutions, Cisco Industrial IoT
Angela Murphy is Senior Global Product Marketing Manager, Cisco Industrial IoT

Content produced in association with Cisco